Web Security Part 1: OCSP

Web applications have become an integral part of our everyday lives and are replacing native applications in all areas of business as well as in private use. Today, no app or social network can function without these technologies. The attack surface that web applications offer attackers is also very extensive and sometimes very easy to exploit.
Nevertheless, many companies still find it difficult to correctly assess the impact and risks posed by vulnerabilities and a lack of defensive measures in web applications.
For this reason, over the next few months we will be addressing a number of topics relating to web application security in our blog series: Web Security.
OCSP & OCSP Stapling
OCSP stands for “Online Certificate Status Protocol” and is used by Certificate Authorities (CA) to monitor the revocation of issued x509 certificates. Clients such as operating systems, applications or browsers can use the OCSP protocol to query the status of a certificate from a validation service. OCSP replaces the outdated CRL (Certificate Revocation Lists) and offers several advantages.
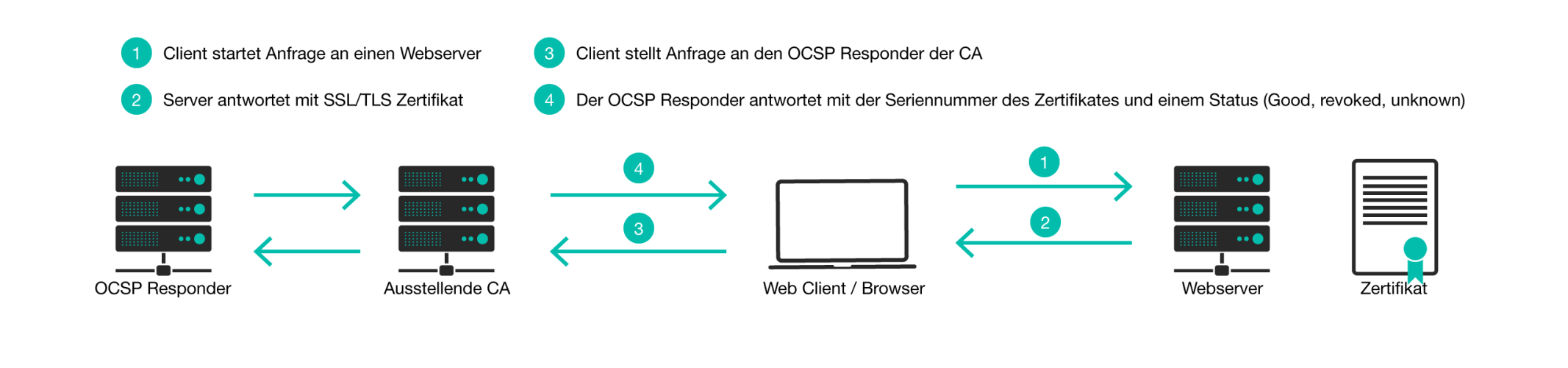
How does OCSP work?
When an SSL/TLS protected connection to a web server is established, the web server first delivers the web server x509 certificate to the client or browser. This certificate contains a CRL or an OCSP responder (or both) in the certificate properties. If the client is configured for this, it prefers to validate the certificate using the OCSP protocol. The client then contacts the OCSP responder with the serial number of the certificate and requests its verification. The OCSP responder checks the certificate either directly in the CA database or in a CRL list and gives the client either the status Good (not revoked) or Revoked (revoked).
Advantages and disadvantages of OCSP and CRLs
Certificate revocation lists are only created and published at longer intervals and are therefore not always up-to-date. OCSP queries are usually issued per certificate and can therefore provide answers to the second. OCSP can also distinguish and recognize forged certificates from valid certificates, provided the OCSP responder has been configured for this by the CA.
When certificate revocation lists (CRL) are used, all revoked certificates are included in this list based on the serial number. This results in relatively large CRL files, which are downloaded on each client. This makes the application inefficient and slow, especially for IoT devices and other devices with limited memory, as the entire file has to be checked for each query.
Another disadvantage of OCSP is that each time a page is requested from a web server, the client makes a request to a third party, the certificate issuer (CA). This not only slows down the access to the website but is also questionable in terms of data protection, as the issuer is informed which certificate and therefore which website is being requested.
To prevent this, OCSP stapling was introduced with RFC6066 (https://clue.ch//clue.ch//tools.ietf.org/html/rfc6066).
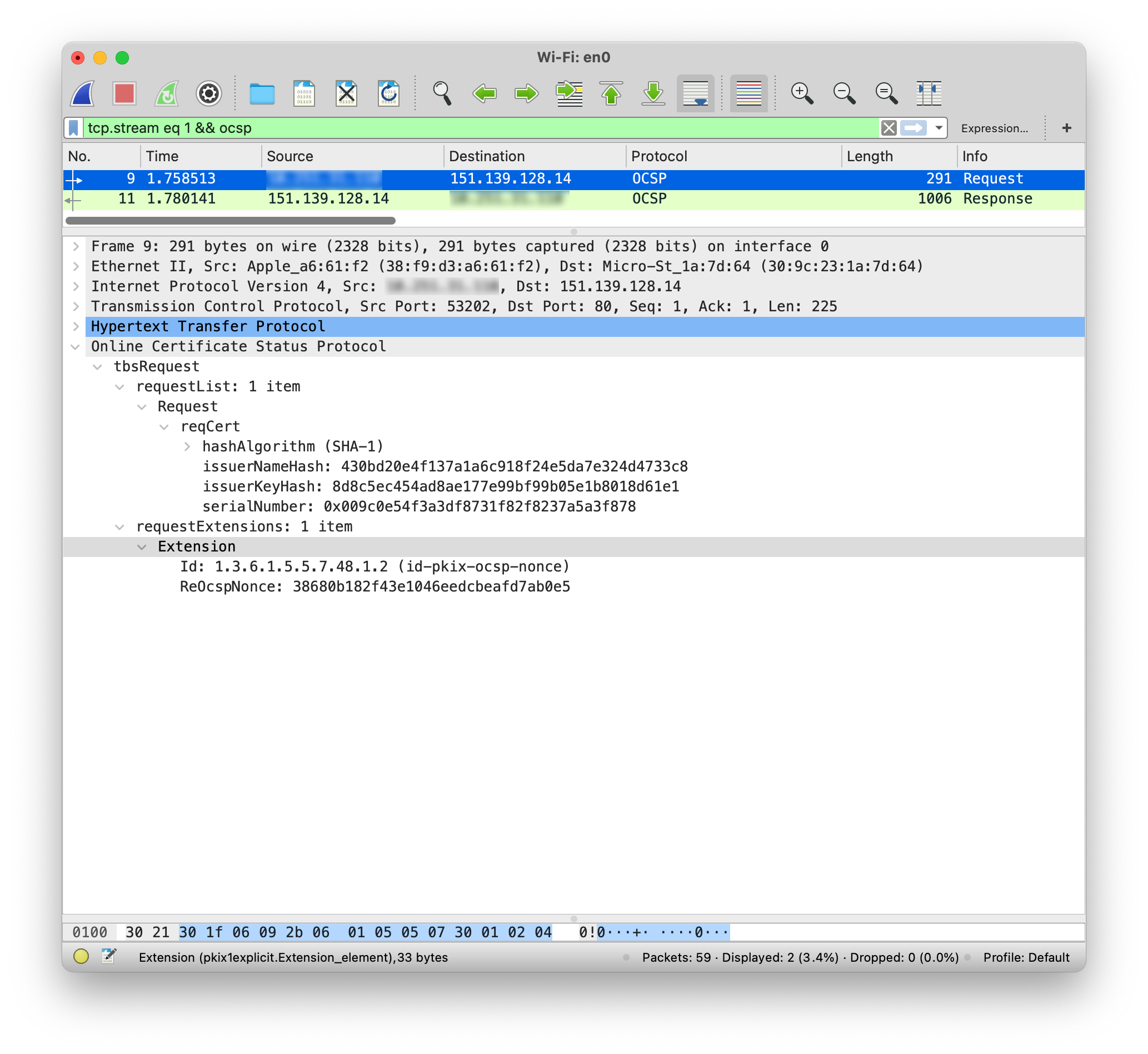
OCSP Request
In the following OCSP request, we see the request to the CA using the determined OCSP protocol. The request contains information about the requested certificate and the nonce extension, which we will explain later.
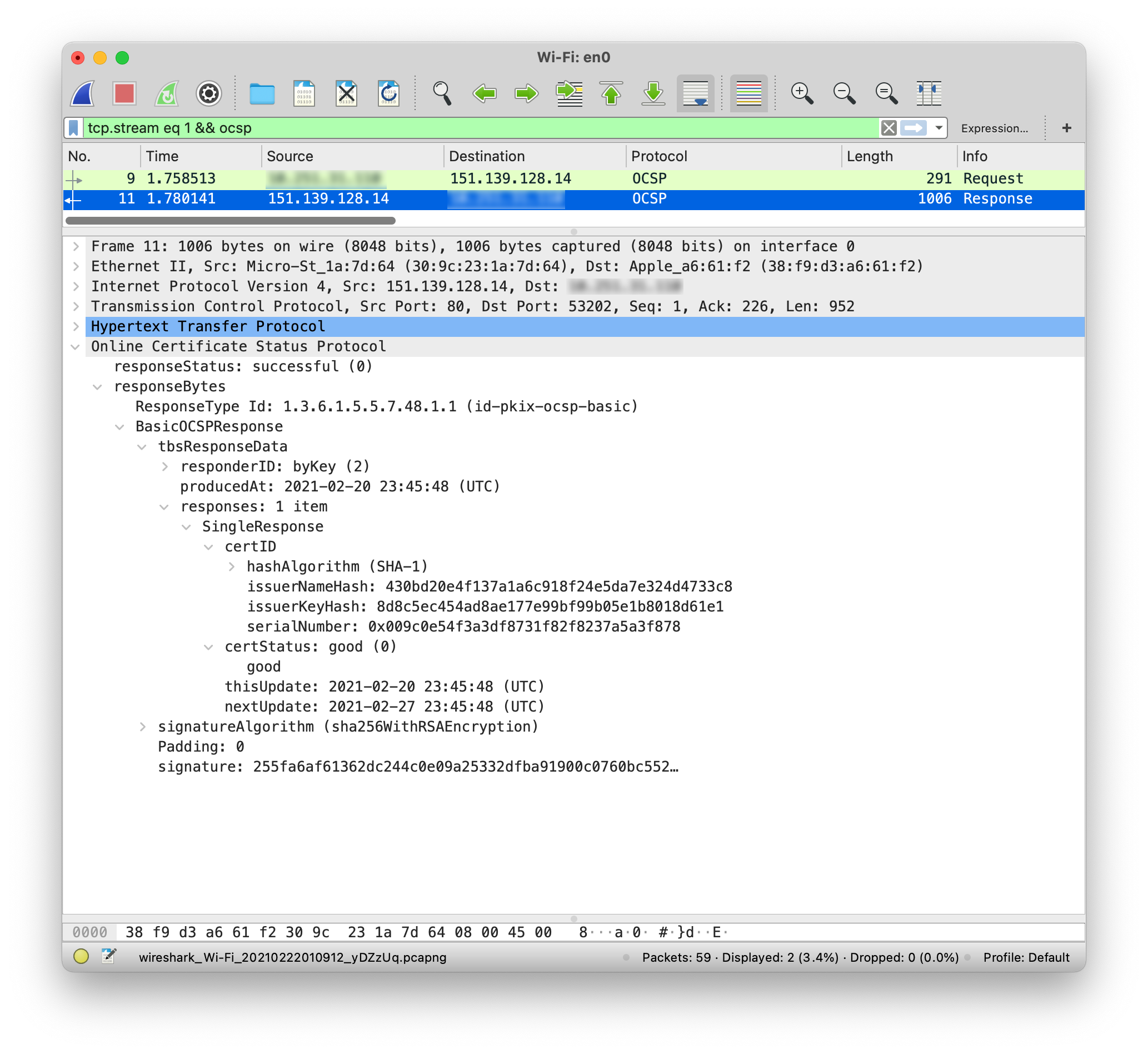
OCSP Response
In the following OCSP response, we see the response from the CA with the certificate status: good. This means that the certificate has not been revoked but there is no indication of the nonce.
What is OCSP stapling?
With OCSP, the client (browser agent) is responsible for requesting the certificate status from the CA. These queries can lead to a delay in accessing the website and also represent a privacy violation, as this query enables the CA provider to log the website accesses. The alternative variant of OCSP stapling was therefore introduced.
When initiating the TLS handshake with the web server, it can send the OCSP validation message with the certificate in the response. This allows the client to complete the request more quickly. The web server acts as a kind of proxy for the OCSP request.
The web server or reverse proxy sends the OCSP request to the OCSP responder and caches the response according to the settings, thereby speeding up the responses to the client.
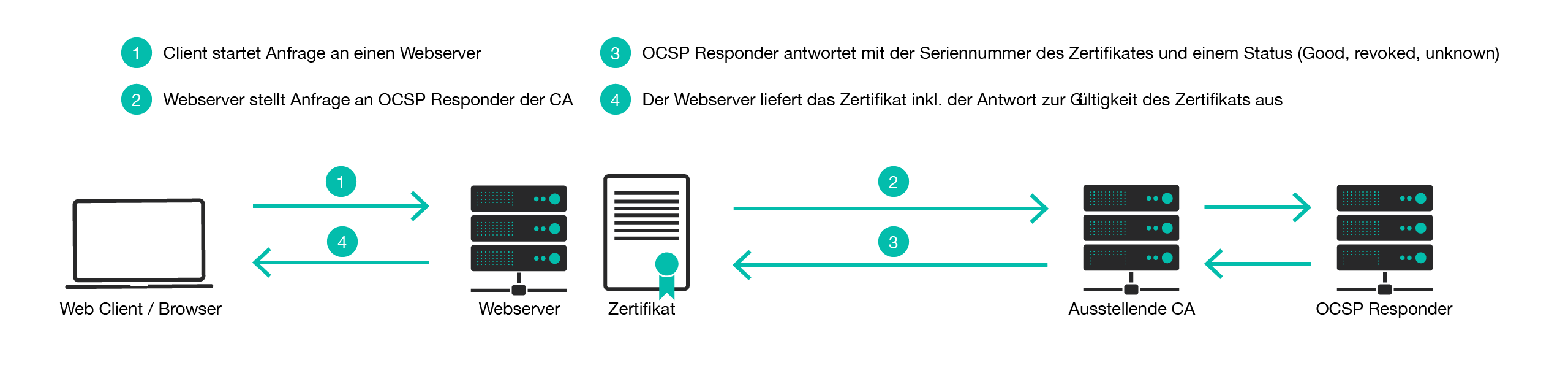
How can I check the OCSP status?
Checking the OCSP status is relatively simple. A few further steps are necessary to query a correct OCSP stapling function. We use the Linux tool openssl in our examples, but the commands could also be executed with curl, for example.
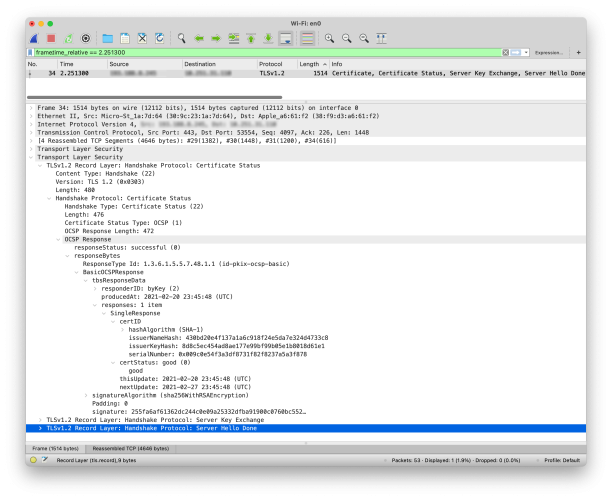
OCSP Stapling Traffic Capture
In this traffic capture you can see that OCSP Stapling does not establish a separate OCSP connection to the OCSP responder, but that the certificate status response is implemented in the TLS confirmation of the web server.
Step 1
First, the server certificate must be requested from the web server
openssl s_client -connect clue.ch:443 < /dev/null 2>&1 | sed -n ‹/—–BEGIN/,/—–END/p› > certificate.pemStep 2
Since SSL certificates are usually never signed directly by the root CA, but by a sub-CA, we request the complete certificate chain.
The first certificate in the chain is the server certificate, we remove it from the chain.crt file
openssl s_client -showcerts -connect clue.ch:443 < /dev/null 2>&1 | sed -n ‹/—–BEGIN/,/—–END/p› > chain.crtStep 3
Now we read the responsible OCSP responder for the server certificate.
openssl x509 -noout -ocsp_uri -in certificate.pem
http://ocsp.sectigo.comStep 4
We have now determined the server certificate, the certificate chain and the responsible OCSP responder. A request can now be made to the service
Specifying the host header is especially necessary for newer OCSP responders, as these do not work using the HTTP 1.0 protocol.
openssl s_client -connect clue.ch:443 < /dev/null 2>&1 | sed -n ‹/—–BEGIN/,/—–END/p› > certificate.pemStep 5
Now we can validate the result. The certificate status can be good or revoked.
OCSP Request Data:
Version: 1 (0x0)
Requestor List:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 430BD20E4F137A1A6C918F24E5DA7E324D4733C8
Issuer Key Hash: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Serial Number: 9C0E54F3A3DF8731F82F8237A5A3F878
Request Extensions:
OCSP Nonce:
04101518B5072B8762A2FC7EC37D7CDB32BD
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Produced At: Feb 19 01:45:49 2021 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 430BD20E4F137A1A6C918F24E5DA7E324D4733C8
Issuer Key Hash: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Serial Number: 9C0E54F3A3DF8731F82F8237A5A3F878
Cert Status: good
This Update: Feb 19 01:45:49 2021 GMT
Next Update: Feb 26 01:45:49 2021 GMTStep 6
We have now been able to validate that the certificate is configured for OCSP and that the OCSP status could be successfully queried from the CA. In this step, we will query the OCSP stapling process through the web server.
openssl s_client -connect cdn.clue.ch:443 -servername cdn.clue.ch -tls1_2 -tlsextdebug -status
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Produced At: Feb 19 01:45:49 2021 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 430BD20E4F137A1A6C918F24E5DA7E324D4733C8
Issuer Key Hash: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Serial Number: 9C0E54F3A3DF8731F82F8237A5A3F878
Cert Status: good
This Update: Feb 19 01:45:49 2021 GMT
Next Update: Feb 26 01:45:49 2021 GMTPossible causes of errors
Nonce
We may receive an error in our response: WARNING: no nonce in response
The warning indicates that our Openssl command has included a nonce as protection against replay attacks, but the server has not confirmed this in its response. This usually happens because certificate authorities want to keep the response times for OCSP requests as short as possible for performance reasons.
In the event that the nonce protection is not answered correctly by the CA, the request can be executed via openssl without nonce using the -no_nonce switch.
openssl ocsp -no_nonce -issuer chain.crt -cert certificate.pem -text -url http://ocsp.sectigo.com -header «HOST» «ocsp.sectigo.com»OCSP response expired
When checking the OCSP configuration, you often see the status OCPS Stapling ok, but also error messages such as “OCSP Response Expired”. This indicates that OCSP stapling is configured, but the web server or reverse proxy cannot query the current status from the CA. The reasons for this could be limited network communication, a fault with the OCSP responder or a lack of trust in the CA based on the x509 certificate chain.

Relationship of trust OCSP Responder
The OCSP service is queried via HTTP protocol. Nevertheless, a signed response is returned as OCSP. Some CAs use the same certificate chain to sign the OCSP responder, while others use a separate certificate chain, such as the GoDaddy CA.
OCSP Response from Sectigo (Comodo)
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Produced At: Feb 20 23:45:48 2021 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 430BD20E4F137A1A6C918F24E5DA7E324D4733C8
Issuer Key Hash: 8D8C5EC454AD8AE177E99BF99B05E1B8018D61E1
Serial Number: 9C0E54F3A3DF8731F82F8237A5A3F878
Cert Status: good
This Update: Feb 20 23:45:48 2021 GMT
Next Update: Feb 27 23:45:48 2021 GMTOCSP Response from GoDaddy
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: C = US, ST = Arizona, L = Scottsdale, O = GoDaddy Inc., CN = Go Daddy Validation Authority – G2
Produced At: Feb 19 20:14:48 2021 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: B6080D5F6C6B76EB13E438A5F8660BA85233344E
Issuer Key Hash: 40C2BD278ECC348330A233D7FB6CB3F0B42C80CE
Serial Number: 98AD27047908DD8B
Cert Status: good
This Update: Feb 19 20:14:48 2021 GMT
Next Update: Feb 21 08:14:48 2021 GMTWhen OCSP stapling is used, the web server or reverse proxy, which in this case makes the request to the actual OCSP responder of the CA on behalf of the client, may not be able to validate the responder’s response.
In this case, the position of trust for OCSP validation must be established. To do this, the validating certificate or the certificate chain is added to the list of issuers to be trusted.
The error is shown, for example, by this error message in the request.
error:27069065:OCSP routines:OCSP_basic_verify:certificate verify error:ocsp_vfy.c:138:Verify error:unable to get local issuer certificateFurther tools
There are many online tools and CLI tools available for analyzing and troubleshooting OCSP and other web security mechanisms.
The following pages are especially helpful for analyzing OCSP configurations.
SSL Labs, an SSL/TLS online test
https://clue.ch//clue.ch//ssllabs.com
CRT.ch, a search engine for x509 certificates
https://clue.ch//clue.ch//crt.sh
Web application firewalls
Web application firewalls act as a reverse proxy and therefore stand between the application user and the web server. The web application firewall (WAF) offers protection mechanisms so that malicious requests to the web server are blocked before they even reach the web server. The WAF not only offers these Layer 7-related security mechanisms but also facilitates a clean configuration of SSL/TLS certificates and protocols, which also includes an OCSP stapling configuration.
Managed Application Protection
Clue Application Protection combines the operation of a web application firewall with the complex protection of your web application. Click here for the service.


